Hashdeep -File Integrity Checker ( CHFI Forensics tool )

CHFI Forensics Practical Training with Hashdeep Tool
Hashdeep - Compute, compare, or audit multiple message digests
Hash deep
is a command line tool. We cannot run the program by double clicking . On Windows,
click on the Start and select Run . Dialog box, just type “cmd.exe”and enter. A
Note: - youcan drag and drop the hash deep icon and the O.S. will
fill in the path information.
HASH COMPUTATION
By
default, hashdeep creates output with a header and then, for each file, the
computed hashes, and the complete name of file .header contains the hashdeep
file version, currently 1.0, which hashes are saved in the file. Hashes are MD5
and SHA-256 hashing algorithm .
%%%% size,md5,sha256,filename
#### Invoked from:
/home/jessek/dir11
#### $ hashdeep config.h INSTALL
READ
####
54533584,db344e43319f900dde2507e7138718b987eda57,28a9b958c3be22ef6bd569bb2f4ea451e6bdcd3b0565c676fbd445533645850b4e670,/home/jessek/dir/config.h
9236,d7adbcf07c5c81369333ddf958be9c40e3,e77137d635c4e9598d64bc2f3f564f36d895d9cfc5050ea6ca75bea33fb6e31ec2,/home/jessek/dir/INSTALL
1609,c15a66414a419644543f8b87f86f7202199a0cc,343f3e1466662a92fa1804e2fc787e89474295f0ab086059e27ff86535dd1065,/home/jessek/dir/README
SYNOPSIS
hashdeep -V | -h
hashdeep [-c <alg1>[,<alg2>]] [-k <file>] [-i <size>] [-f <file>] [-o
<fbcplsde>] [-amxwMXreEspblvv] [-F<bum>] [-j <num>] [FILES]
DESCRIPTION
Computers multiple hashes, or message digests, for any number of files. While optionally recursively digging through the directory structure. By default, the program computes MD5 and SHA-256 hashes, equivalent to -c md5,sha256.It Can also use a list of known hashes to audit a set of files. Errors are reported to standard error. If no files are specified, reads from standard input.
CHFI v9 certification Role –
CHFI Training Course was designed to provide you with the software and techniques used by security professionals alike to monitor an organization’s security. They will be introduced to an entirely different way of achieving information security posture in their organization; by monitoring it! They will be able to pen test their own systems.
CHFI v9 is the world's advanced Forensics course with 14 of the most current security subtopics any Ethical Hacker will ever want to know when they are planning to check the information security posture of their organization. This training prepares you for EC-Council Security Analyst.
You will also gain knowledge about Intrusion Detection Systems (IDS), Policy Creation, Social Engineering Techniques, Dos & DDoS Attacks, Buffer Overflow Attack and Virus Creation Techniques. When you leave this intensive training you will have hands on understanding and experience in Forensics and will have the knowledge and skills required to sit for the EC-Council ANSI accredited Security Analyst Exam.
Use Of Hashdeep –
- Navigate to forensics tool in kali linux .you can find hashdeep there.

- Create Hash of a file - Command – Hashdeep filename
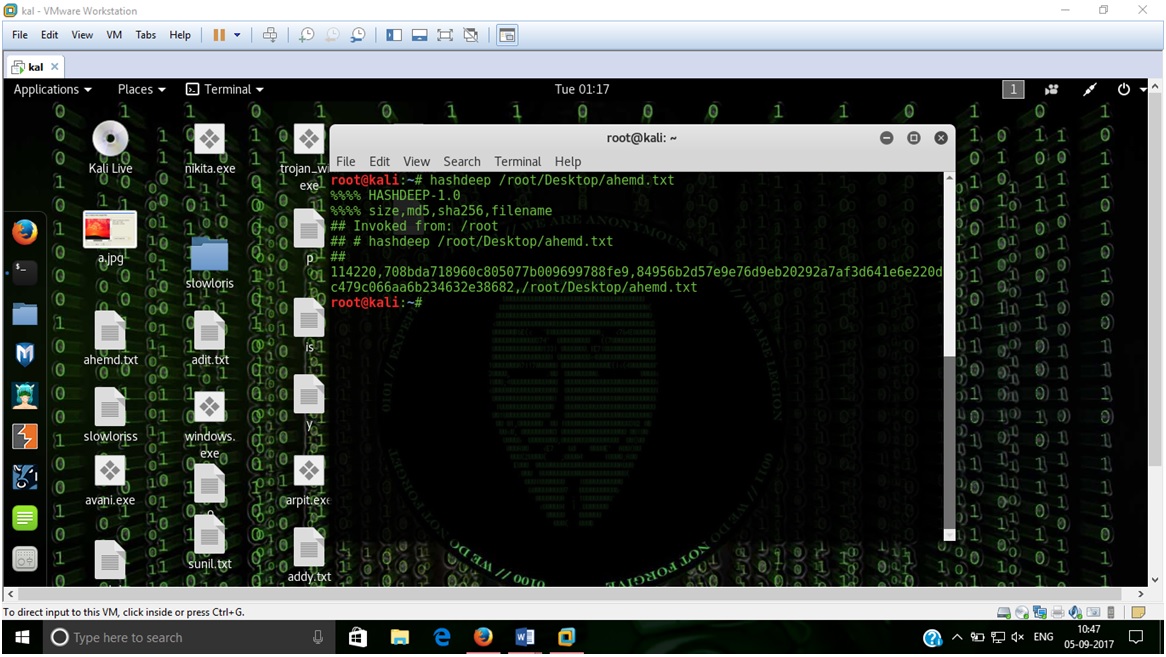
- If a user make changes in the content of file , hash changes accordingly –

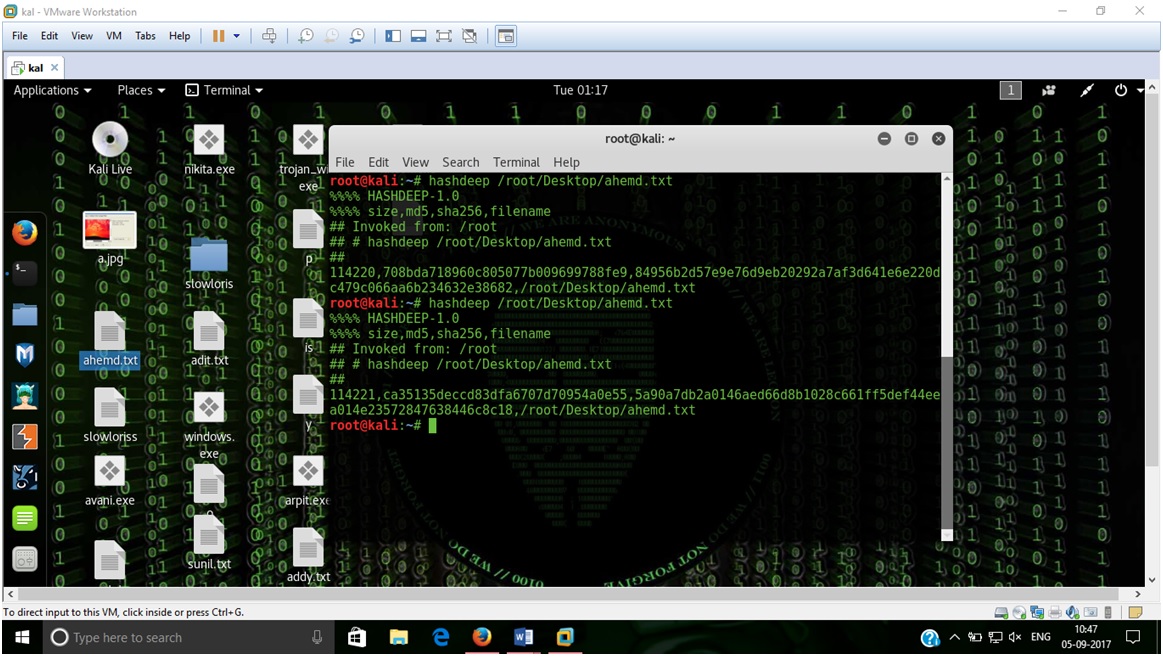
-- By Sunil Gupta (Web Security Specialist)
Comments
Post a Comment