HOW TO HACK WIRELESS NETWORKS
How Are Wireless Networks Hacked?
The CEH Certification is the greatest of the most wanted information security training program some cyber security expert will ever need to be in. We offer training of CEH certification in Delhi With expert.
Codec Networks is one of the best training institutes for CEH training in Delhi.Our training fully based on practical and project. Our trainers are expert in their profile. Classes are available in
week days and weekends also.
WEP (Wired Equivalent Privacy)
Wired Equivalent Privacy (WEP) is a security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standards ratified in 1997, its intention was to provide data confidentiality comparable to that of a traditional wired network. WEP is recognized by its key of 10 or 26 hexadecimal digits (40 or 104 bits) and was used widely. It was the first security choice presented to users by router configuration tools. In 2003 the WEP had been suspended by Wi-Fi Protected Access. The IEEE declared the removal of WEP-40 and WEP-104 from Wi-Fi Secure access.
The WEP encryption consists of 8 or more numerical keys that can be used for authentication for connecting to the wireless networks. These keys can be easily cracked using the different algorithms.
WPA (Wi-Fi Protected Access)
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access II (WPA2) are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks The Wi-Fi Alliance intended to develop more secure Wi-Fi password encryption called WPA2.It was WPA2 was available in 2004.
This is the most secure alternative and cracking of the passphrase of such a network requires the use of a wordlist or a dictionary with words which are similar to the passphrase key. In other words, cracking WPA2 networks works with the old trick of hit and trial, where different words are compared with the log packets and the matching words together give out the password. WPA-2 is the most secure encryption till today. This is considered to be virtually uncrackable with a strong password.
WEP passwords can be recovered or exploited very easily.
What You'll Need
- Wireless Adapter
An external wireless adapter is required for searching the wireless networks around you. Nowadays laptops are already equipped with wireless adapters.
- CommView for Wi-Fi:
CommView captures the packets of the desired network and creates the log files which can be used to crack the Wi-Fi password. Click here to download the software from their website. The download link for CommView is given below
http://www.tamos.com/download/main/ca.php
- Aircrack-ng GUI:
Aircrack-ng is used for cracking the password out the captured the packets. Click here to download the software from their website. The download link for Aircrack-ng GUI is given below
http://www.aircrack-ng.org/
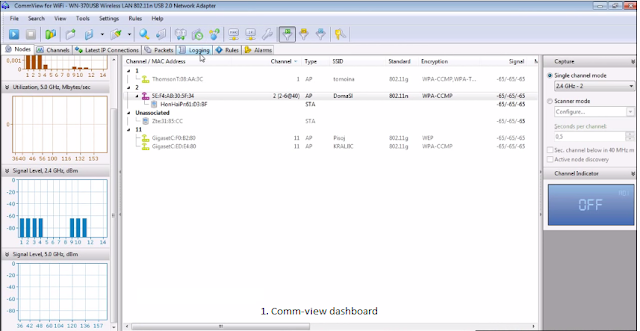
Setting Up CommView for Wi-Fi
- Download the CommView from the website. And run the exe file.
- Run CommView for Wi-Fi.
- Click the play icon on the top left of the application window.
Scanning for wireless networks is started.
Wait for some time and you will get a list of all wireless networks around you.
Selecting the Target Network
For selecting the target wireless network:
- The network should be running on WEP encryption.
- The network should have the highest signal or transmission power.
Once the target network is selected, click on Capture to start capturing packets of the desired target network.
It is noticed that the log packets are being captured from all networks, you need to capture packets only from the desired network
- Right click on the target network and select copy MAC Address.
- Open the Rules tab From the top.
- Choose MAC Addresses from the left side on the top.
- Execute MAC Address rules.
- Select “Capture” for action and “Both” for recording.
- Now paste the mac address copied earlier in the dialog box below.
Capturing Packets
For saving the data packets logs, select D on the bar at the top of the window and deselect M (Management packets) and C (Control packets).
You need to save the packets so that they can be cracked later. To do this:
- Go to the logging tab on top and enable auto saving.
- Set Maximum Directory Size as 2000.
- Set Average Log File Size as 20.
Saving the logs helps a lot more logs you save more easily the password will be cracked.
This is the most important part of the password cracking, so be patient.
After you think you have enough packets (at least 100,000 packets), you'll need to export them.
- From Logging tab , click on “concentrate logs”.
- Select all the logs saved by the CommView.
- Go to the folder where the logs are saved.
- Open the saved log file.
- Select File- Export -Wire shark tcpdump format & save it to any suitable destination.
- This will save the logs with a .cap which are readable by the Aircrack-no.
CRACKING
- Download Aircrack-ng and extract the compressed file.
- Open the extracted folder and open 'bin'.
- Executive Aircrack-ng GUI.
- Select WEP option.
- Open the .cap files saved earlier.
- Click Launch.
- In the command prompt type in the index number of your target wireless network.
- Wait for a some time.
If everything is ok, the WEP key will be shown.
IF receive a request to try with more packets, again start capturing the packets using CommView.
Role of an ethical hacker
An ethical hacker’s role is similar to that of a penetration tester, but it involves broader duties. They break into systems legally and ethically. This is the primary difference between ethical hackers and real hackers—the legality. Then, there is a requirement of Network Security Specialist to diagnose and fix the Vulnerabilities.
According to the EC-Council, the ethical hacking definition is “an individual who is usually employed with an organization and who can be trusted to undertake an attempt to penetrate networks and/or computer systems using the same methods and techniques as a malicious hacker.”
We are Best Institute for Ethical hacking Training in Delhi. Codec Networks provides Ethical hacking certification in Delhi Centre with Lab Facility. We prepare for latest CEH V9 Training in EC Council; candidates need to work on a live project.
Codec Networks Professional training from EC Council and Israel company Cyber Security Hacker U Pro, we provide an environment exactly like the actual one where they will be taught how to perform information gathering, scanning, getting access i.e. hacking, maintaining access, clearing tracks as well as how to secure their own networks.



Comments
Post a Comment